如letsencrypt官方说明所述:开放 80 端口并不会在服务器中引入更大的攻击面,因为 80 端口和 443 端口通常由同样的软件提供服务。但是如果确实你的Web服务器通过防火墙封闭了80端口,而且你仍旧希望从 Let’s Encrypt 获取证书,您有两种选择:您可以使用DNS-01验证方式,或(在443端口上)使用支持TLS-ALPN-01验证方式的客户端。
下面记录我通过DNS验证的方式为nginx申请Certbot证书的过程。
一、环境信息
- Debian GNU/Linux 10;
- certbot 1.19.0;
- 通过DNS验证方式申请证书;
二、操作步骤
2.1 更新系统
sudo apt update
2.2 安装Nginx
设置Nginx仓库地址
echo "deb http://nginx.org/packages/debian `lsb_release -cs` nginx" \
| tee /etc/apt/sources.list.d/nginx.list
执行安装
apt install nginx
这里假设你的网站根目录是/root/www
启动nginx
sudo systemctl start nginx
sudo systemctl enable nginx
我的nginx配置如下:
#/etc/nginx/conf.d/4spaces.org.conf
server{
listen 8080;
server_name v4.xxxx.com;
index index.html;
root /root/www/;
}
访问地址:http://v4.xxxx.com:8080/。
2.3 安装certbot
安装snapd
apt install snapd
确保snapd为最新版本
sudo snap install core; sudo snap refresh core
删除certbot-auto以及相关CentOS包
sudo dnf remove certbot
sudo apt-get remove certbot
安装certbot
sudo snap install --classic certbot
创建软链
sudo ln -s /snap/bin/certbot /usr/bin/certbot
2.4申请证书
进行申请
root@debian-4:~# certbot -d v4.xxxx.com --manual --preferred-challenges dns certonly
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): winbert.w@gmail.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Account registered.
Requesting a certificate for v4.xxxx.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
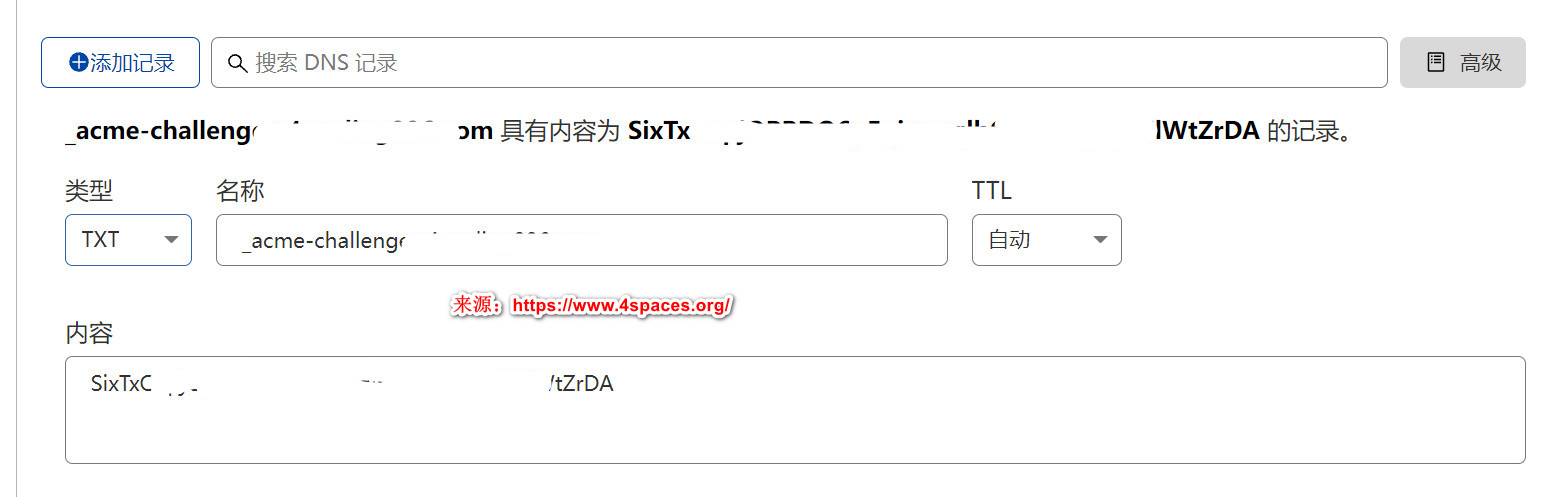
Please deploy a DNS TXT record under the name:
_acme-challenge.v4.xxxx.com.
with the following value:
SixTxOcpjQPBDO6pEgjwseqlbQJNY-iq0qZUlWtZrDA
Before continuing, verify the TXT record has been deployed. Depending on the DNS
provider, this may take some time, from a few seconds to multiple minutes. You can
check if it has finished deploying with aid of online tools, such as the Google
Admin Toolbox: https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.v4.xxxx.com.
Look for one or more bolded line(s) below the line ';ANSWER'. It should show the
value(s) you've just added.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
根据提示设置DNS
在你域名解析中添加一条TXT记录,名称为上面提示的_acme-challenge.v4.xxxx.com,值为提示的SixTxOcpjQPBDO6pEgjwseqlbQJNY-iq0qZUlWtZrDA,然后等待你的DNS记录设置生效。
继续证书申请
DNS设置生效后,回到证书申请界面,回车。
Press Enter to Continue
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/v4.xxxx.com/fullchain.pem
Key is saved at: /etc/letsencrypt/live/v4.xxxx.com/privkey.pem
This certificate expires on 2021-12-24.
These files will be updated when the certificate renews.
NEXT STEPS:
- This certificate will not be renewed automatically. Autorenewal of --manual certificates requires the use of an authentication hook script (--manual-auth-hook) but one was not provided. To renew this certificate, repeat this same certbot command before the certificate's expiry date.
We were unable to subscribe you the EFF mailing list because your e-mail address appears to be invalid. You can try again later by visiting https://act.eff.org.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
至此证书申请完毕。
2.5 配置Nginx
server{
server_name v4.xxxx.com;
index index.html;
root /root/www/;
listen 9090 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/v4.xxxx.com/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/v4.xxxx.com/privkey.pem; # managed by Certbot
}
server{
if ($host = v4.xxxx.com) {
return 301 https://$host:9090$request_uri;
} # managed by Certbot
listen 8080;
server_name v4.xxxx.com;
return 404; # managed by Certbot
}
References:
1.最佳实践——开放 80 端口;
2.How to use Let’s Encrypt DNS challenge validation?;
3.Correct way to completely remove issued certificate(s) for a domain;
4.吊销证书;
5.无80端口情况下使用 CertBot 申请证书并使用nginx更新证书;
6.无80端口情况下使用 CertBot 申请SSL证书 并实现自动续期;




最新评论
什么时候出新版啊已经过了半个月了
有没有港台节目直播?
One Drive提取密码?
大佬请问每次都需要在plugins中启动tiktok吗,还是直接启动app